
canary
Assume Breach, Detect Early: The Power of Canaries
Why canary signals outperform conventional detection and reduce mean-time-to-discovery

zerotrust
Recently, I needed to publish a simple website for a small community, nothing fancy, but I didn’t want to open any unnecessary holes. I wanted it secure. I also wanted caching to save bandwidth and CPU (cheap hosting). I wanted to do all of this while minimising the risk
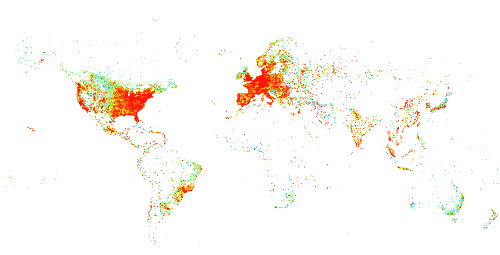
asm
Once upon a time I was sat in departures at DBX and needed to to quickly enumerate all virtual machines in an Azure tenant, to find out how many had a particular vulnerable service exposed cough omi cough. It needed to be quick... 80/20 rule was good enough to

microsoft
One of the biggest gaps in enterprise defence has always been consistent, automated endpoint security, and if you've ever wrestled with Group Policy or tried to keep hybrid devices compliant you'll appreciate just how far Microsoft Intune has come. Last week Microsoft published a new dedicated
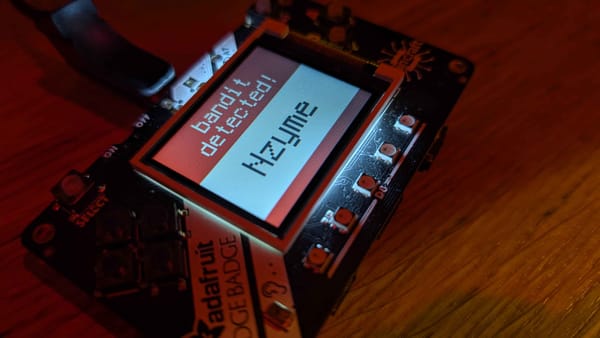
bsides
When I first set up Nzyme and took it to BSides London, it was missing something pretty important: a way to alert me properly when chaos broke out. At the time, the only supported alerting mechanism was email, and while that worked in theory, it didn’t quite fit the

incident-response
In today’s hyper-connected world, businesses and individuals are more intertwined than ever, operating in a digital ecosystem where even the smallest players are part of a vast, interdependent network. This unprecedented level of connectivity creates opportunities, but it also introduces significant risks. The reality is that cyberattacks are inevitable.
wifi
Through my interest in securing systems and networks, I’m always looking for new ways to compromise things and detect attacks. One area I’m always watching is Wi-Fi security. It’s come a long way since I first broke into a wireless network (we can talk about that another

cyber
Providing software and SaaS services to financial institutions requires a deep understanding of security, compliance, and operational resilience. Banks and financial firms operate under strict regulatory frameworks and have zero tolerance for security failures. Regulatory requirements such as APRA CPS 234 in Australia, the UK Cyber Security and Resilience Act,
Information and Cyber Security, Technology & Leadership