Experimenting with Nzyme: Building a Wireless Intrusion Detection System
Through my interest in securing systems and networks, I’m always looking for new ways to compromise things and detect attacks.
One area I’m always watching is Wi-Fi security. It’s come a long way since I first broke into a wireless network (we can talk about that another time). The landscape has shifted massively, and today there’s a huge range of both offensive and defensive tools available.
On the defensive side, clients often ask:
Do you use wireless networks in the transfer or processing of sensitive data?
Do you have WIDS (Wireless Intrusion Detection Systems) in place?
And these are legitimate questions, there are legitimate risks.
From a compliance point of view, deploying WIDS is mentioned in multiple frameworks.
PCI DSS v4.0 Requirement 11.2.1 explicitly requires detection of unauthorized wireless access points. NIST SP 800-53 Rev 5 SI-4 and CIS Controls v8 call for continuous monitoring to identify rogue devices and anomalous wireless activity, while ISO/IEC 27001 & 27002 include intrusion detection under broader network management and access control requirements. Even NIST CSF 2.0 and Zero-Trust models emphasize continuous telemetry, including wireless, as part of maintaining situational awareness.
Historically, implementing WIDS has been expensive and complex, while attacks have become commoditized with devices such as the Hak5 Wi-Fi Pineapple, and democratized via a few minutes of YouTube and a laptop running Kali Linux... with few open-source options worth considering.
And then, a few years ago, that changed.
Discovering Nzyme
Nzyme.org : Nzyme safeguards against close-access threats by using real-time data from on-site sensors, integrating wireless and wired telemetry to create denied environments.
It’s built by Lennart Koopmann, the founder of Graylog, the log aggregation and SIEM tool many of us have used. When I found out he’d built an open-source platform for wireless threat detection, I knew I had to try it.
An open-source system I could build cheaply, using commodity hardware, to detect and analyse wireless activity? Perfect.
So I built a deployment for experimentation and then decided to take one of the taps to London’s premiere cybersecurity conference, BSides London.
Nzyme can detect
The Build
Using commodity hardware and public cloud, I set up a small but capable Nzyme environment:
- 3× Raspberry Pi devices
- Panda USB Wi-Fi adapters
- An Azure instance running the Nzyme node
- Tailscale for secure, mesh-based communication
- Cloudflare Zero Trust to safely publish the Nzyme web interface
Each Pi acts as a tap, capturing Wi-Fi frames from the air and forwarding them to the central Nzyme node, which aggregates the data, displays it in a web interface, and generates alerts.
This is all very cool, but what can it actually detect?
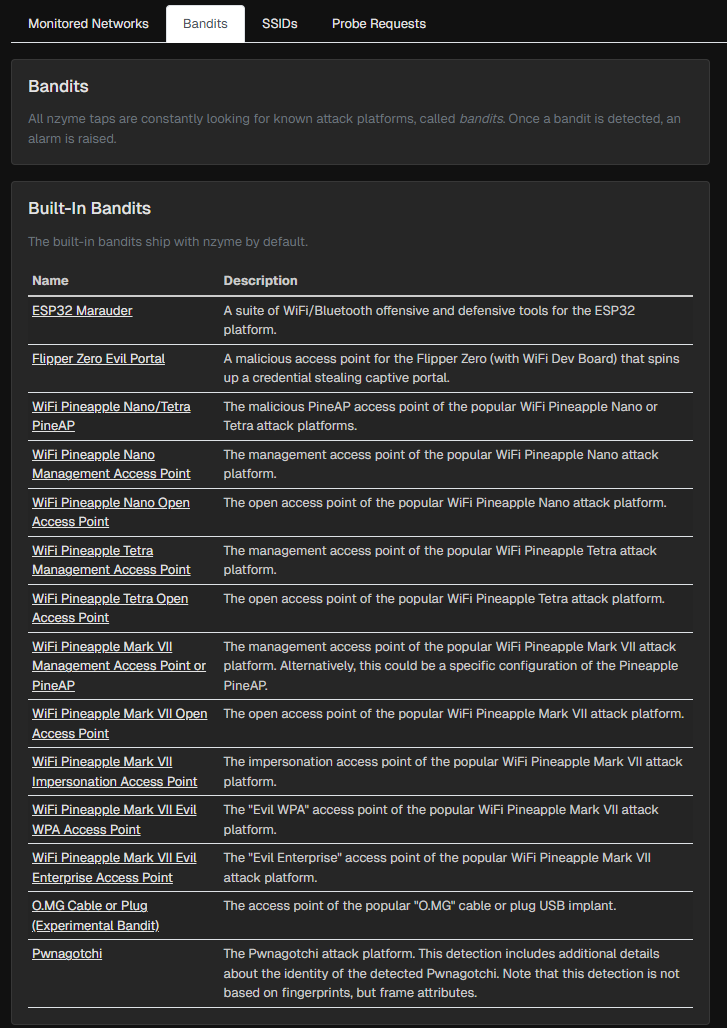
- Known Wi-Fi attack hardware such as Pwnagotchi, Wi-Fi Pineapple, or ESP32 Marauder boards.
- Common wireless attacks, including de-authentication or disassociation floods that force clients to reconnect.
- Evil Twin access points, define your legitimate SSIDs, MACs, and ciphers, and Nzyme can detect imposters attempting to mimic your infrastructure.
Basic Deployment
My deployment looked like this:
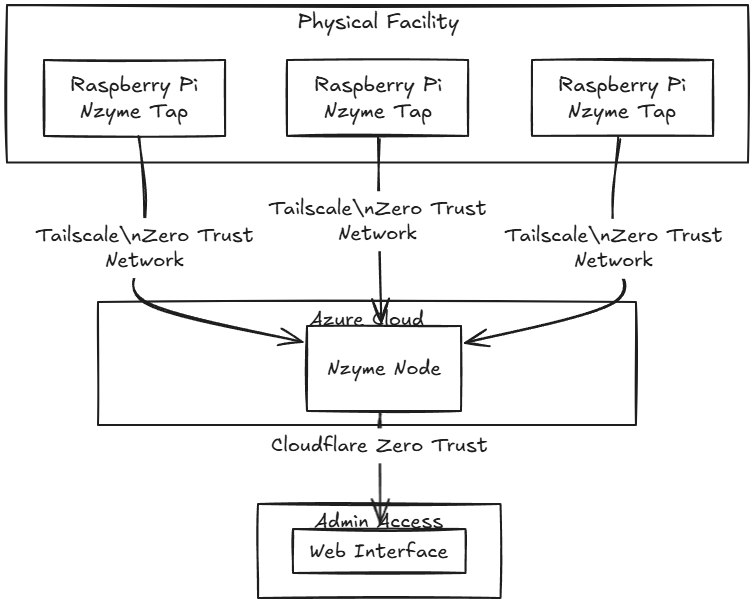
- Nzyme Node: central server for collecting tap data, issuing alerts, and configuring monitored networks. Runs Nzyme node and PostgreSQL.
- Taps: Raspberry Pis with Panda Wi-Fi adapters to capture frames.
- Network: secured with Tailscale, a mesh-WireGuard zero-trust network for encrypted communication between taps and node.
- Web Application: published through Cloudflare Zero Trust, allowing secure access anywhere permitted by policy.
(Nzyme also has its own authentication and MFA.)
Taking the tap to BSides was easy - a Raspberry Pi powered by an Anker power bank, tethered to a mobile hotspot, talking back to the node via Tailscale.
Capabilities
Nzyme provides a surprisingly rich feature set for an open-source tool:
- Central configuration and system overview
- Mapping and trilateration of device locations
- Bandit tracking (persistent identification of suspicious devices)
- Environment learning and baselining
- Real-time alerts and event forensics
Real-World Test: BSides London
Deploying Nzyme at BSides was mostly for fun but it quickly turned into a live testbed.
At first, nothing unusual appeared:
- My own Pwnagotchi and Wi-Fi Pineapple were detected exactly as expected.
- Normal background noise from hundreds of attendees’ devices filled the spectrum.
- Lots of funny SSID from attendees' hotspots and devices
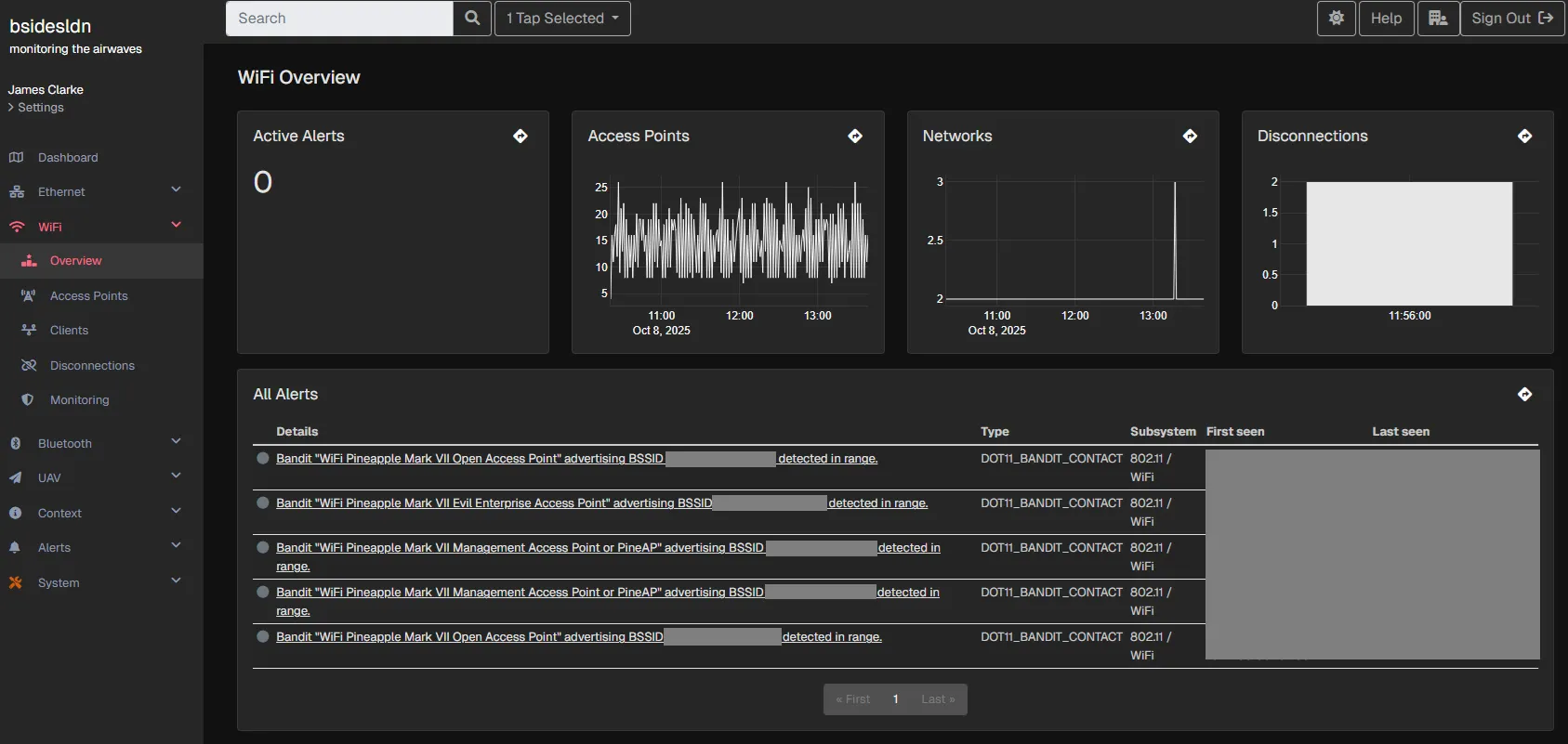
And then, someone powered up a Wi-Fi Marauder and began spamming SSIDs.
Within seconds, the Nzyme alerting interface lit up, effectively DoS’ing itself with floods of new alerts.
But that was the point: it saw everything.
It caught the SSID spam, recorded the event timelines, and made it clear just how much chaos one cheap ESP32 board can cause.

It was a great showcase of how Nzyme turns invisible RF noise into something actionable and understandable.
The Future
These are capabilities we didn’t use at BSides but which Nzyme already supports or has on its roadmap:
- Bluetooth device detection and enumeration
- UAV / drone detection and location
- Ethernet monitoring, to spot suspicious beacons, C2 traffic, or malware callbacks
Together, these point toward a broader vision: unifying air and wire visibility into a single situational-awareness platform.
References
Closing Thoughts
Running Nzyme at BSides London was a great reminder of how little visibility most of us have into the airspace around our networks.
With a handful of Raspberry Pis, some open-source code, and a secure overlay network, it’s possible to build a functional, low-cost Wireless Intrusion Detection System that rivals enterprise tools in capability.
If you’re serious about understanding what’s really happening over the air, or just want a fun, hands-on project, Nzyme is well worth a weekend of your time.